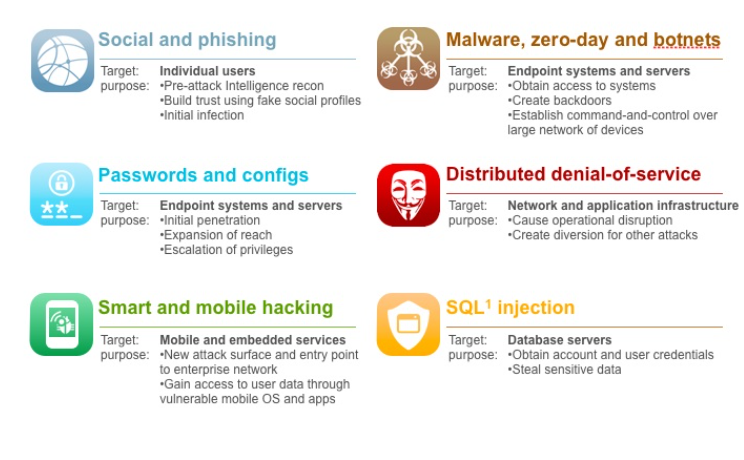
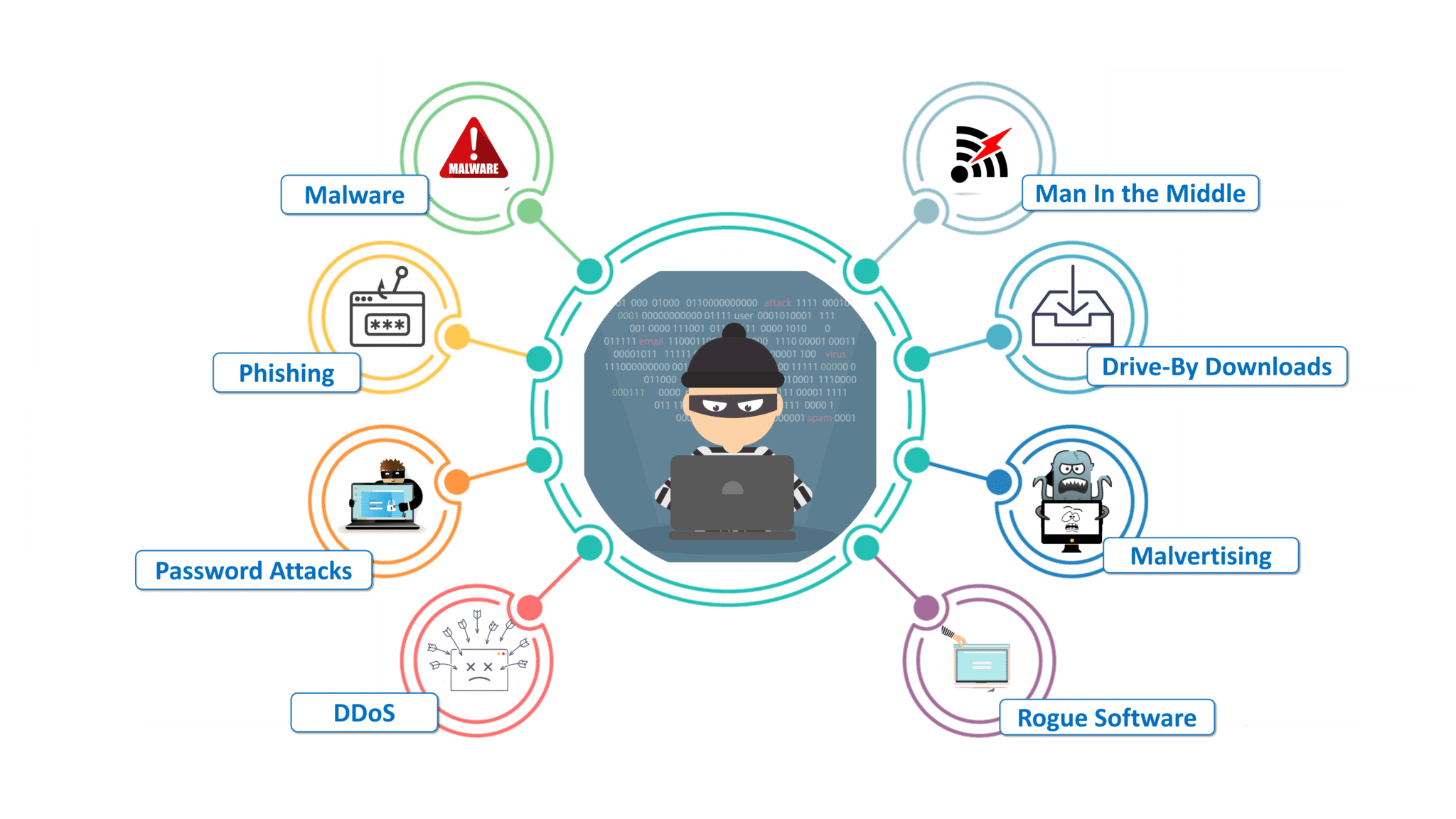
In today's world, many of us deal with lots of challenges daily. An individual's spirit is tested daily as we should compete with these various difficulties. keeping their PC secure and well preserved is an obstacle faced by lots of individuals. There are typically professionals studying most challenges, looking for much better ways of handling them.
You most likely answered "yes" to at least a few of these concerns. So, if you look at your life you will find frustrating proof that you are a capable and competent individual. Although you may not be perfect, all the things you carry out in your life is actually quite exceptional. Think of this a bit. Don't take it for granted. Consider all your remarkable capabilities and accomplishments.
Today, unlike years back, there are numerous kinds of individual security and self security devices readily available. Individual alarms are small and fit in any handbag or pocket-- they even clip to your belt. These alarms release a really loud noise that will get anyone's attention. Also, pepper spray can be found in various camouflaged containers-- pagers, pens, key chains and even lipstick!

If you get an email which contains a link to a major anti-virus software application concern, or genuine known Web security source, it's likely a genuine virus that's being cybersecurity gone over. However, DO NOT click any of the links. Instead, check out the site itself by typing the URL into your internet browser directly.
Individuals who run billion dollar corporations are obese. People who run countries Cybersecurity Threats are obese. Individuals who make revolutionary scientific discoveries are obese. Individuals who bring and develop out the most intricate strategies are obese. Are all these people all of a sudden weak when it pertains to food?
It wasn't like it is today when I went to college. Coeds could walk alone during the night on campus and feel relatively secure. However today, with colleges becoming so large, the car park, labs, research study halls and the library seem to be in darker and more far-off areas.
You may be having an alarm or video camera system installed. Do you understand if the installer is legal? Lots of business's stop working to have a look at their installers. They think the security company has actually done their task and the person is ok. This is the wrong method to believe. This is your building, your security or camera system, your defense versus criminal offense, why would you not take a look at everyone.
If you are brand-new to computers, this procedure would certainly be too made complex for you to do. So instead of the manual technique, you may desire to remove the fake program using the automated removal procedure. All you need is leading performing software that can do the work. It is shown to save time and you'll be back enjoying your time in the Web in no time. This method also ensures elimination of the whole bad program and will continue to keep your computer system safe from future risks.